See What See
We use the same OSINT reconnaissance techniques as threat actors - breached credentials, dark web monitoring, attack surface mapping - then show you exactly how they'd compromise your organization. The difference? We report. They exploit. Free exposure check available. Full briefing is a paid engagement — schedule a call to confirm fit.
// paid_executive_briefing | call_confirms_fit_and_scope
// HIGH_VALUE_TARGETS
Industries that threat actors actively hunt. Is your sector on their list?
// RECON_SCAN.INIT
Run the same reconnaissance attackers use. See what they see.
$ ./scan_target.sh
// passive_mode=true | network_access=false
[+] free_scan | [+] no_credentials_required | [+] instant_results | [!] email_must_match_domain
[SCAN_COMPLETE]
-[!] Quick preview only. The Executive External Exposure Briefing includes: breach cost analysis, framework predictions, insurance impact, red team simulation, attack path mapping. This briefing is a paid, executive-level engagement. The call is to confirm fit and scope.
Schedule Executive Briefing Call →// ABOUT.CYBER_RISK_SNAPSHOT
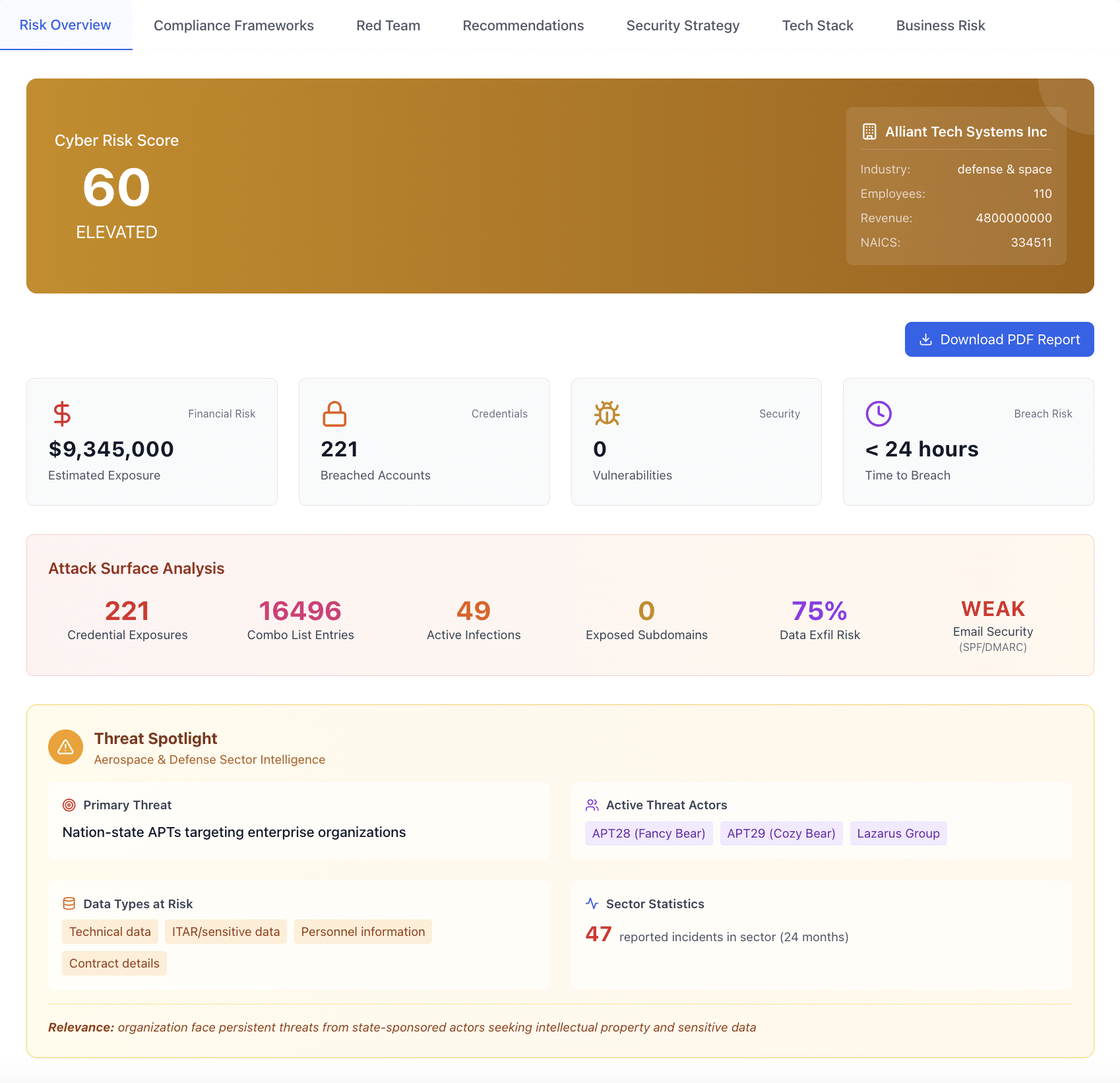
The Cyber Risk Snapshot is adversary-grade reconnaissance that shows you exactly what attackers see when they target your organization. No agents, no network access - pure OSINT tradecraft.
But we don't just dump raw data. We translate findings into business impact: breach cost estimates, insurance implications, compliance gaps, and competitive positioning - language your board and investors understand.
- Breach Cost Analysis - Estimated exposure using IBM's Cost of Data Breach methodology
- Compliance Framework Prediction - Identifies which frameworks apply to your business
- Insurance Impact Assessment - How findings affect your cyber insurance position
- Red Team Attack Simulation - 5-phase attack path modeling with success probabilities
// INTEL_MODULES
What the recon reveals. Technical findings + executive translation.
Breached Credentials & Infostealers
Employee credentials in data breaches and dark web markets. Includes infostealer infections with session cookies that bypass MFA entirely.
Identity RiskExternal Attack Surface
Exposed subdomains, development environments, shadow IT, and forgotten infrastructure that attackers use as entry points.
Infrastructure RiskVulnerability Analysis
Externally visible CVEs ranked by EPSS exploitation probability - focus on what's actually being exploited, not theoretical risk.
Technical RiskCompliance Framework Prediction
Automatically identifies which frameworks (SOC 2, HIPAA, PCI-DSS, ISO 27001, GDPR, etc.) likely apply based on your industry and business model.
Compliance RiskBreach Cost Analysis
Estimated financial exposure using IBM's methodology. Per-record costs, operational disruption, ransomware recovery estimates.
Financial RiskRed Team Attack Simulation
5-phase attack path modeling based on your actual exposures. See how adversaries would chain findings into a successful breach.
Attack Simulation// DAMAGE_ASSESSMENT
Security findings translated into metrics your board understands
// SIGNAL_VS_NOISE
Raw data is useless. Context is everything. We show why it matters.
Not This
"You have 523 CVEs and 89 breached credentials"
Raw numbers without context create noise and paralysis. Leadership can't prioritize.
We Deliver This
"Your estimated breach cost is $2.3M. Here's the attack path and what to fix first."
Business impact with prioritized remediation. Leadership can make decisions.
Not This
"You should consider SOC 2, ISO 27001, HIPAA, PCI-DSS..."
Generic compliance checklists that don't consider your actual business model.
We Deliver This
"Based on your healthcare clients and revenue, HIPAA applies with 94% certainty"
Framework predictions based on your industry, size, and customer base.
// FRAMEWORK_DETECTION
Automatic compliance prediction based on industry, size, and business model
// FAQ.LOG
Common questions about the recon process
Will this scan touch our network?
No. The Cyber Risk Snapshot is 100% passive OSINT. We only query external intelligence sources - we never scan your systems, install agents, or access your internal network.
How is this different from a vulnerability scan?
Vulnerability scanners probe your systems. We show what's already publicly exposed - breached credentials, dark web mentions, leaked data - things scanners can't see.
What if we're already SOC 2 certified?
Great! We'll show you what attackers see despite your certification. SOC 2 is about controls, not exposure. Many certified companies have significant external risk.
Can I share the report with my board?
Yes - that's the point. Reports include executive summaries with business impact metrics, not just technical jargon. Built for leadership consumption.
How accurate is the breach cost estimate?
We use IBM's Cost of Data Breach methodology with your industry averages, employee count, and risk multiplier. It's an estimate, but a data-driven one.
Do you sell remediation services?
We're advisory-first. We provide recommendations and can help with compliance readiness, but we're not trying to upsell you managed services or tools.
// READY_TO_ENGAGE?
See exactly what threat actors see. Before they do. Full briefing is a paid engagement — schedule a call to confirm fit.
// paid_executive_briefing | call_confirms_fit_and_scope
The Cyber Risk Snapshot is a comprehensive cybersecurity risk assessment for private sector organizations. Using passive OSINT reconnaissance, we reveal breached credentials, exposed infrastructure, and vulnerabilities - then translate findings into business impact analysis including breach cost estimates, insurance implications, and compliance gap identification. Our platform predicts applicable compliance frameworks (SOC 2, HIPAA, PCI-DSS, ISO 27001, GDPR) based on your industry and business model. Ideal for healthcare organizations, financial services, SaaS startups, and any business that needs to understand their cyber risk posture. Based in Philadelphia, HostBreach provides security assessments, compliance advisory, and risk management for organizations serious about protecting sensitive data.
