Cyber Insurance Underwriting Powered by OSINT
Cyber insurance underwriting requires more than questionnaires. Get external attack surface intelligence, credential exposure data, and breach history on applicants before you bind coverage.
Book a 15-Minute CallTraditional Cyber Insurance Underwriting is Broken
Cyber insurance underwriting has relied on self-reported questionnaires and static compliance checklists. These methods fail to capture the dynamic nature of cyber risk and are prone to errors and omissions.
OSINT-powered cyber insurance underwriting gives you the attacker's view of each applicant: what's actually exposed, what credentials are compromised, and what incidents may have gone unreported.
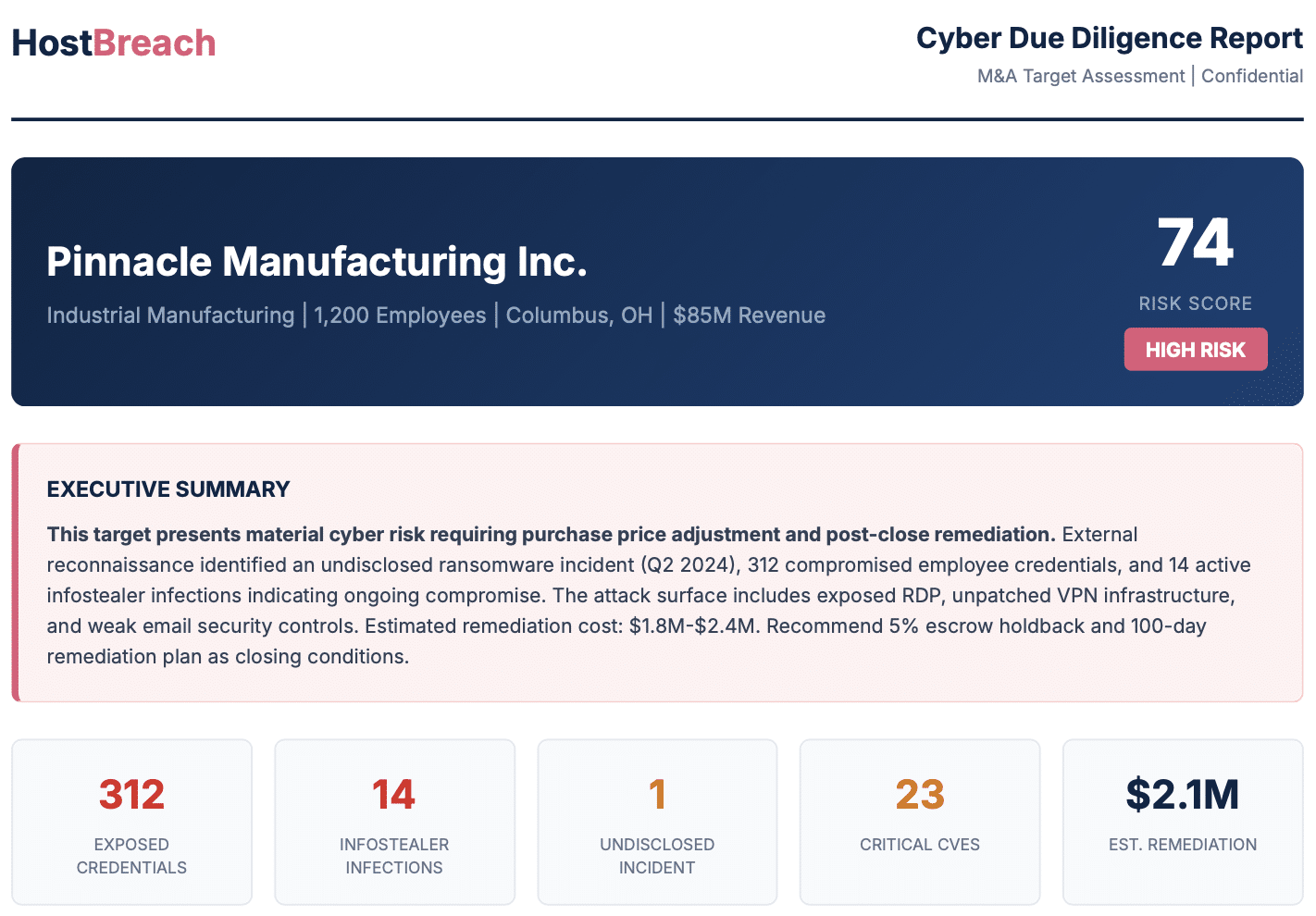
OSINT for Underwriters
External intelligence throughout the policy lifecycle
Pre-Binding Assessment
External reconnaissance on applicants before you quote. Verify questionnaire responses against actual attack surface exposure and credential leakage.
Premium Pricing
Risk-based pricing with quantifiable security metrics. Credential exposure, breach history, and attack surface data inform accurate premium calculations.
Renewal Assessment
Track security posture changes between policy periods. Identify new exposures, remediated issues, and evolving risk profiles for renewal decisions.
Intelligence for Better Cyber Insurance Underwriting
What questionnaires miss, OSINT reveals
Credential Exposure
Employee credentials in breach databases and infostealer logs. Active session tokens that bypass MFA. Indicators of ongoing compromise.
Claims PredictorInfostealer Infections
Real-time infostealer malware detections. Harvested credentials, cookies, and session tokens. Leading indicator of imminent breach.
High Risk SignalBreach History
Past security incidents including unreported events. Ransomware attacks, data leaks, and threat actor attribution from dark web intelligence.
Prior LossAttack Surface
External-facing assets, exposed services, and shadow IT. Known CVEs on internet infrastructure. Misconfigured remote access and cloud resources.
Exposure DataEmail Security
SPF, DKIM, DMARC configuration status. Spoofing and phishing vulnerability. BEC fraud risk indicators critical for social engineering coverage.
BEC RiskSecurity Controls
Evidence of security tooling from external indicators. WAF, CDN, and security vendor relationships. Compliance framework signals.
Controls VerificationQuestionnaires vs. OSINT
See what you've been missing
| Capability | Questionnaires | OSINT Intelligence |
|---|---|---|
| Credential exposure visibility | ✗ Self-reported, often unknown | ✓ Actual breach database & infostealer data |
| Real-time attack surface | ✗ Point-in-time snapshot | ✓ Live external asset discovery |
| Undisclosed breach history | ✗ Relies on applicant disclosure | ✓ Dark web & threat intel sources |
| Email security verification | ✗ "Yes we have email security" | ✓ Actual SPF/DKIM/DMARC analysis |
| Active compromise indicators | ✗ Not detectable | ✓ Infostealer infections, session tokens |
| Verification of responses | ✗ Trust-based | ✓ Evidence-based validation |
Better Cyber Insurance Underwriting Decisions
Our intelligence reports give underwriters the external view they need to make informed decisions, price risk accurately, and avoid adverse selection.
- ✓ Risk scores based on actual exposure, not self-reporting
- ✓ Credential exposure counts for accurate pricing
- ✓ Breach history verification including undisclosed incidents
- ✓ Attack surface metrics for exposure quantification
- ✓ Email security analysis for BEC coverage decisions
- ✓ Delivered in hours, not weeks
Applicant: TechCorp Industries
Risk: MEDIUMUnderwriting Note: No active compromise indicators. Moderate credential exposure from historical breaches. DMARC gap increases BEC risk - consider email fraud sublimit or require remediation pre-bind.
Improve Your Underwriting Process
Get OSINT-powered risk intelligence on applicants. Better data means better underwriting decisions, accurate pricing, and reduced claims.
