External CUI Intelligence Aligned to How Are Actually Compromised
HostBreach applies adversary-view intelligence informed by DC3 DIB reporting to reveal unauthorized initial access risk, clarify enclave vs. full-organization CMMC scoping, and prioritize CMMC Level 2 remediation — without questionnaires or internal access. Free exposure check available. Full briefing is a paid engagement — schedule a call to confirm fit.
This is a paid executive briefing. The call is to confirm fit and scope.
Free Quick Risk Check
Get a preview of your external exposure. The full CMMC Cyber Snapshot is delivered via consultation.
Check Your Domain Exposure
100% passive OSINT - we never touch your network
✓ Free preview • ✓ No credit card • ✓ Results in seconds • ✓ Email must match domain (e.g., you@company.com for company.com)
OSINT Assessment:
-This is just a quick preview. The Executive External Exposure Briefing includes red team attack simulation, CUI-handling personnel targeting, CMMC control mapping, and Enclave vs. Full-Org strategy recommendations. This briefing is a paid, executive-level engagement. The call is to confirm fit and scope.
Schedule Executive Briefing Call →What is the CMMC Cyber Snapshot?
The CMMC Cyber Snapshot is a proprietary intelligence platform built by HostBreach. We don't just run vulnerability scans - based on our analysis of DC3 DIB threat intelligence, we show you the exact attack vectors being used to breach defense contractors today.
Based on your external OSINT exposure and our red team attack simulation, we provide prioritized recommendations (not affirmations) mapped to CMMC Level 2 controls. You'll understand whether an Enclave or Full-Org approach makes sense for your organization - without filling out lengthy questionnaires.
- DC3 DIB Threat Intelligence - Based on our analysis of how contractors actually get breached
- Recommendations, Not Affirmations - Prioritized actions based on real exposure, not checkbox compliance
- Enclave vs. Full-Org Insight - Understand your CUI strategy without questionnaire fatigue
- 100% Passive OSINT - No network access, no agents, no disruption to operations
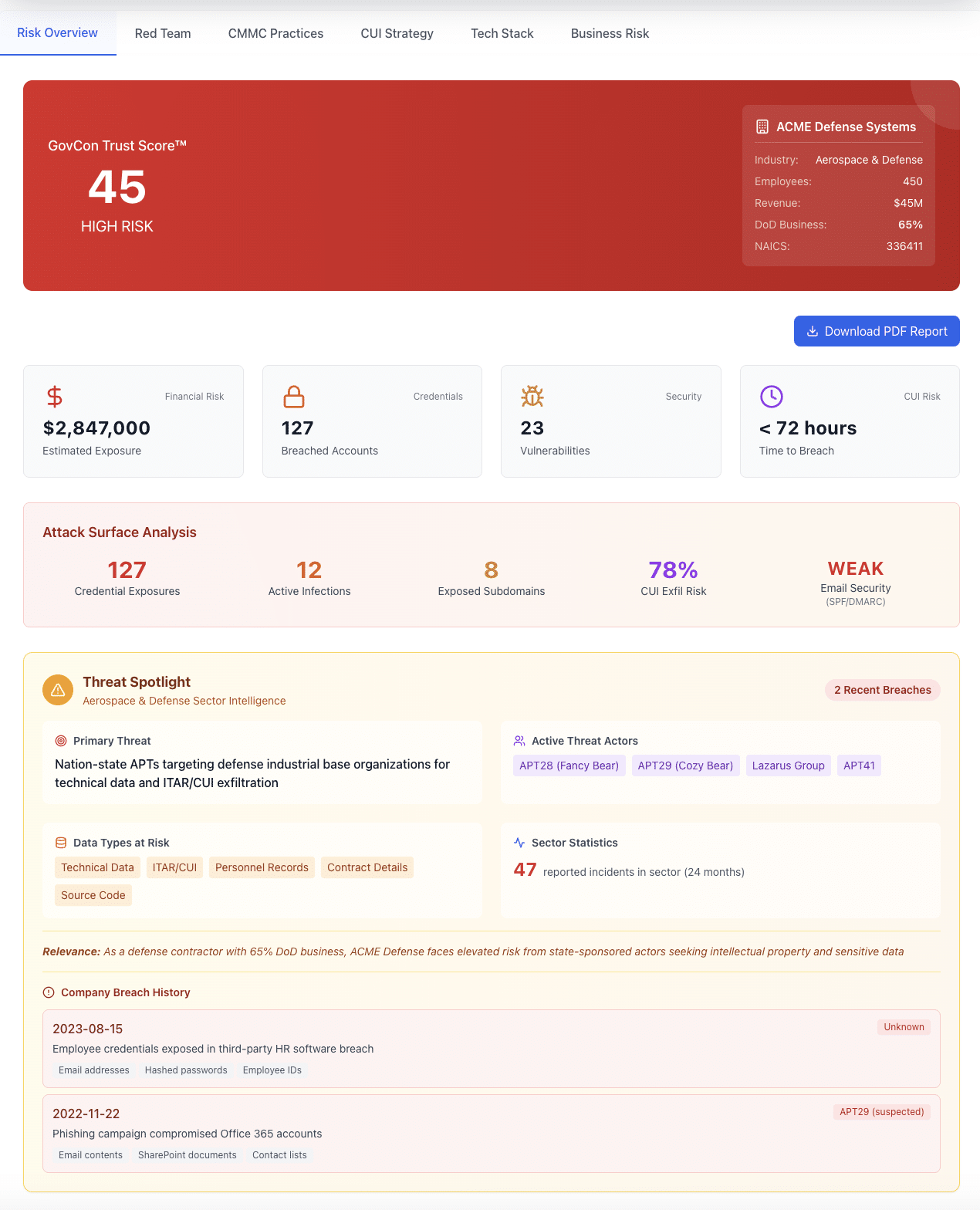
The Exact Attack Vectors Breaching DIB Contractors
Based on our analysis of DC3 DIB threat intelligence and MITRE ATT&CK techniques, we simulate the same reconnaissance adversaries use. We show you what they find - before they exploit it.
[FOUND] Active DoD contracts detected - CMMC L2 required
[INTEL] Scanning breach databases for employee credentials...
[INTEL] Querying infostealer log marketplaces...
[INTEL] Enumerating subdomains and shadow infrastructure...
[ATTACK PATH] dev.contractor.com exposed - internal tools accessible
[ATTACK PATH] CFO email in combo list - potential BEC target
[T1539] Steal Web Session Cookie → [SI.L2-3.14.2] Detect and remediate malicious code
[T1190] Exploit Public-Facing App → [AC.L2-3.1.20] Control external system connections
// SECTOR_THREAT_FEED
Live threat intelligence from the Aerospace & Defense sector
What the CMMC Cyber Snapshot Reveals
6 intelligence modules powered by 20+ OSINT sources. Prioritized recommendations mapped to CMMC Level 2 controls based on your actual exposure.
Breached Credentials & Infostealers
Employee credentials exposed in data breaches and actively sold on dark web markets. Includes infostealer malware infections with captured session cookies that bypass MFA.
IA.L2-3.5.x ControlsExternal Attack Surface
Discover exposed subdomains, development environments, forgotten VPNs, and shadow IT that attackers use as initial access points into your network.
SC.L2-3.13.x ControlsCVE Vulnerabilities with EPSS
Externally visible vulnerabilities ranked by EPSS exploitation probability - not just CVSS scores. Know which CVEs are actually being exploited in the wild.
SI.L2-3.14.x ControlsEmail Security Analysis
SPF, DKIM, and DMARC configuration analysis. See if attackers can spoof your domain for phishing campaigns targeting employees or partners.
SI.L2-3.14.x ControlsCUI-Handling Personnel Targeting
We identify key personnel (Program Managers, Engineers, Executives) who handle CUI and would be prime targets for spear phishing campaigns by APT actors.
Red Team IntelCUI Strategy Recommendation
Based on your DoD revenue percentage (40% threshold), we recommend either an Enclave or Full-Organization approach to CUI handling - no questionnaires required.
Enclave vs Full-OrgContext, Not Just Data
We don't bombard you with vulnerability lists or meaningless IOCs. We show leaders why findings matter to your business.
Not This
"You have 847 CVEs across your infrastructure"
Raw vulnerability counts without prioritization overwhelm teams and provide no actionable direction.
We Deliver This
"3 CVEs on your VPN are actively exploited - here's the attack path to your CUI"
Prioritized findings with business context showing exactly what needs attention first.
Not This
"127 employee emails found in breach databases"
Breach counts without context don't tell you which credentials actually pose risk to CUI.
We Deliver This
"Your Program Manager handling CUI is a prime spear phishing target - here's why"
Key personnel identified as attack targets with role-based risk context.
4-Phase APT Attack Simulation
Our AI models exactly how adversaries would use your exposures to breach your organization and exfiltrate CUI. Based on MITRE ATT&CK and real-world intrusion data.
Initial Access
Using breached credentials and exposed services to establish foothold
Persistence
Establishing backdoors and disabling security controls
Lateral Movement
Moving through network using discovered access
Exfiltration
Extracting CUI via cloud services and encrypted channels
Prioritized Recommendations, Not Checkbox Compliance
Based on your OSINT exposure and simulated attack paths, we recommend which CMMC controls to prioritize - actionable guidance, not generic affirmations.
14 CMMC Domains Covered
- Access Control (AC)
- Identification & Authentication (IA)
- System & Communications Protection (SC)
- System & Information Integrity (SI)
- Configuration Management (CM)
- Risk Assessment (RA)
- + 8 More Domains
CRITICAL Breached Credentials → IA.L2-3.5.3 (T1078)
Recommendation: Credential exposure impacts identity assurance. Prioritize MFA enforcement and credential resets. Supporting: AC.L2-3.1.1 for access limitation.
HIGH Infostealer Infections → SI.L2-3.14.2 (T1539)
Recommendation: Session cookies bypass MFA - detection and remediation is critical. Investigate affected endpoints and establish incident handling per IR.L2-3.6.1.
HIGH Shadow Infrastructure → AC.L2-3.1.20 (T1190)
Recommendation: Exposed dev/staging environments are a boundary control issue. Evaluate external connections and establish configuration baselines per CM.L2-3.4.1.
MEDIUM Email Spoofing Risk → SC.L2-3.13.1 (T1566)
Recommendation: SPF/DMARC misconfiguration is a communications integrity problem. Harden email security to protect against phishing and BEC attacks.
Frequently Asked Questions
Common questions about the CMMC Cyber Snapshot
Will this scan touch our network?
No. The CMMC Cyber Snapshot is 100% passive OSINT. We only query external intelligence sources - we never scan your systems, install agents, or access your internal network.
How long does the scan take?
Most scans complete in 2-5 minutes. Comprehensive analysis with AI-powered attack simulation takes slightly longer but results are available within minutes, not weeks.
Is this a CMMC assessment?
No. This is a pre-assessment intelligence tool that provides recommendations based on your external exposure. Our findings are prioritized suggestions, not compliance affirmations. We can refer you to C3PAOs for formal certification.
Can I share the report with assessors?
Yes! Reports are executive-ready and can be shared with C3PAOs, internal teams, or leadership. Many clients use our findings to prioritize remediation before their assessment.
What if we're not a DoD contractor?
We also offer a Private Sector Cyber Snapshot that maps to frameworks like SOC 2, HIPAA, and PCI-DSS. Contact us for details.
How is this different from a pentest?
Pentests actively probe your defenses. The Cyber Snapshot shows what's already exposed externally - breached data, leaked credentials, shadow IT - without any active testing.
Ready to See What Attackers See?
Run your free exposure check and get actionable intelligence before your assessment. Full briefing is a paid engagement — schedule a call to confirm fit.
This is a paid executive briefing. The call is to confirm fit and scope.
The CMMC Cyber Snapshot is a proprietary pre-assessment intelligence platform built by a CMMC advisory firm. Aligned with DC3 DIB Cybersecurity threat reports, we show Defense Industrial Base contractors the exact attack vectors being used to breach organizations like yours. Our platform reveals breached credentials, infostealer infections, and exposed infrastructure - then provides prioritized recommendations (not affirmations) mapped to CMMC Level 2 controls. Understand your Enclave vs. Full-Org CUI strategy without questionnaires. Based in Philadelphia, HostBreach provides CMMC readiness services, gap assessments, and advisory for DoD contractors handling Controlled Unclassified Information (CUI).
